30 Recommended Ideas For Choosing A Dubai Cyber Security Service
30 Recommended Ideas For Choosing A Dubai Cyber Security Service
Blog Article
Top 10 Tips On How To Evaluate The Experience And Credibility Of A Cyber Security Firm In Dubai Uae
1. Assess Industry Experience
It is important to look for firms who have extensive experience working in the field of cybersecurity. You can find out how long the business has been operating and whether they've worked with companies similar like yours. A business with good track records will be able to understand your particular needs and problems.
2. Review Client Portfolio
To gauge the depth and breadth of expertise, take a look at the company's portfolio. Companies that have been successful in working across multiple industries, particularly ones relevant to yours and those you are looking to work with, demonstrate flexibility and versatility when it comes their cybersecurity services.
3. Look over Case Studies for Success Stories
Request case studies that show the success of the business in dealing with cybersecurity issues. Provide examples of how they have been able to reduce risks or solve issues for clients will help you gain a better knowledge of their capabilities.
4. Research Online Reviews and Ratings
Search for ratings and reviews on sites such as Google, copyright or forums that are specific to your field. Positive reviews from customers can prove a company's reputation. However, negative reviews can raise alarms. Take note of recurring themes.
5. Connect with Industry Peers
Join a network of peers to receive recommendations and information on cybersecurity service providers. Interacting with people who have direct experience of a company will give you valuable information about the reliability and effectiveness of a company.
6. Consideration of Contributions and Thought Leadership
Consider how your company's contributions to the cybersecurity community can be seen in its thought leadership. This can be done through whitepapers that are published as well as participation in industry conferences or contributions to cybersecurity forums and blogs. Companies that share their expertise generally gain respect and credibility.
7. Check professional certifications and affiliations.
It is also possible to check for professional certifications, partnerships or partnerships with the top tech companies. The company's association with well-known cybersecurity or technology firms can show that it is a reputable company within the field.
8. Find out about the qualifications of the staff
Check the experience and credentials of your team members. Examine for certifications such as copyright or CISM among the team. A team with high qualifications can improve a business's image in managing cybersecurity security risks.
9. Evaluate response to security incidents
Investigate past incidents of security breaches. Their ability to react to incidents will indicate their level and expertise. Understanding how they handle emergencies can provide you with an insight into their performance.
10. Search for awards and recognition
Look for any awards or awards the company won in the field of cyber-security. Awards in the industry can be indicators of a firm's excellence and reputation. Recognizing organizations with a good reputation usually demonstrate a commitment to professionalism and top quality. Have a look at the best Cybersecurity Company in Dubai for website advice including network security and, it security jobs, it security services company, ai and cybersecurity, network security systems, network and network security, cyber security services near me, cyber security information, it security description, network security tools and more.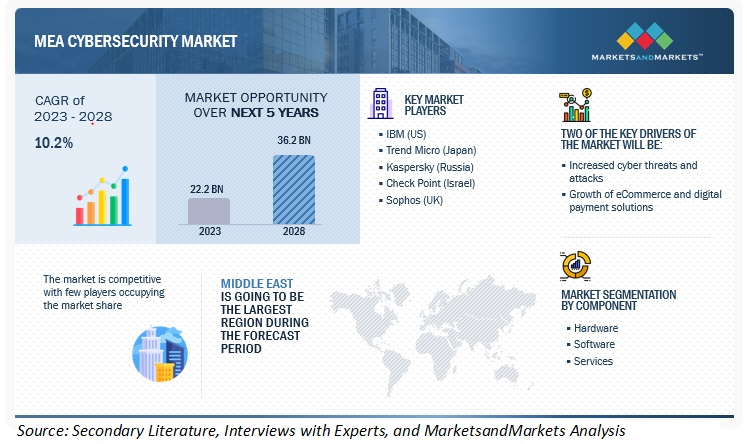
Top 10 Ways To Evaluate The Technology And Tools Of A Cybersecurity Company Located In Dubai, Uae
1. Technology StackStart with an evaluation of the technology stack employed by the business. It includes hardware, software and tools. A robust and diverse technology stack means that the business is well-equipped to deal with a range of cybersecurity challenges efficiently. Look for modern tools that align with industry standards.
2. Assess Security Solutions Offered
Examine the specific solutions offered by the company like endpoint security as well as security information event management (SIEM). Knowing the offerings of the company will allow you to determine whether their security solutions will are a good fit for your needs.
3. Integrate your capabilities
Consider how well the tools and technology of your company work with existing systems. Integration that is seamless is crucial in ensuring security is secured and interruptions are reduced. You should ask what they do to integrate their new technologies with the existing infrastructure.
4. Request Information on Automation and AI
Examine if the company uses artificial intelligence and automation for its cybersecurity processes. AI helps in identifying threats, improving security and efficiency.
5. Keep an eye out for regular updates
Find out about the company's management of patches and software updates. Updates are vital to protecting yourself from new threats and vulnerabilities. An active approach to maintaining your tools demonstrates a commitment to safety.
6. Evaluation of Vulnerability Assessment Tools
Examine the tools used by your company and processes to manage weaknesses. Effective vulnerability scanning is essential for identifying weaknesses and fixing the weaknesses. You should inquire how they prioritize weaknesses and then addressing the issues.
7. Review Incident Response Technologies
Know the tools your company uses for response to incidents. Efficient incident response tools can greatly reduce the damage caused by an attack on security. Ask the technology-driven incident management framework.
8. Analytical Reporting Tools
Examine and compare the tools' reporting and analysis capabilities. Comprehensive reporting provides insights into security postures, incident trends and compliance status. Make sure the analytics tools you use are effective and enable data-driven decision-making.
9. Cloud Security Solutions - Inquire now!
Given the rise of cloud computing, assess the company's cloud security solutions. Businesses that heavily rely cloud-based services must know how to protect their cloud environments and safeguard the information they save in the cloud.
Customer Feedback Reviews
Last, ask existing customers for their feedback about the effectiveness of the technology and tools employed by your business. Testimonials or case studies that highlight the effectiveness of a particular technology could give you valuable insight into their practical applications. Take a look at the top rated penetration testing dubai for website examples including cyber security technology, data and security, network security, cyber security risks, cyber security what, network it security, cyber technologist, cyber security ot, it security services company, managed it services security and more.
Top 10 Tips On How To Evaluate The Contracts And Pricing Structure Of A Cybersecurity Service Company
1. Know Pricing ModelsStart by familiarizing yourself with the various pricing models employed by the business. Some common models are fixed-price contracts as well as hourly rates. Understanding these models helps you to determine what will fit your budget best and how costs accumulate over time.
2. Request detailed quotes
Ask for detailed quotes that detail all expenses associated with the service. Clear quotes should contain service descriptions, costs and any additional charges. Clarity in pricing can help avoid unexpected costs.
3. Think about Service Packages
Find out if the business provides service bundles. Bundling your services can be more cost-effective than purchasing them individually. Take a look at the bundles available to see if they meet your needs and can provide financial advantages.
4. Find out about additional costs.
Do not hesitate to inquire about hidden charges. This could be overtime charges as well as travel costs and the cost of emergency support. Understanding total costs is critical in budget planning.
5. Flexible Contracts: An Overview of the Choices
Check the contract flexibility. It is important to determine whether the contract allows the flexibility to modify your requirements and to scale down or up the services offered. Contracts with too much rigidity can cause unnecessary costs or hinder the flexibility of services.
6. Check for long-term commitment requirements
Understand if there are any long-term commitment requirements associated with the pricing structure. Some companies may provide lower rates for extended agreements, but this could lock in a long term commitment. Be aware of the benefits versus risk if your requirements change.
7. Reconsider the Termination Clauses
Learn the conditions in which you are able to end the agreement, as well as any penalties associated with it. Know the conditions for terminating the agreement as well as any penalties. An acceptable cancellation policy provides you the opportunity to exit in the event that services do not meet your expectations.
8. Review the payment terms
Find out about the terms of payment. Know when the payment will be due, if you can make payments in installments and if you can get an advantage for paying in advance. The clarity of the payment terms will aid in cash flow management.
9. Clarifications regarding SLA Penalties
Review the Service Level Agreements, especially the penalties for failure to meet service levels. Knowing these penalties can provide insight into the commitment of the business to quality service.
10. Compare yourself with your competitors
The comparison of the pricing structure to other cybersecurity service providers in Dubai as well as the UAE will help you to evaluate the worth of your investment. Benchmarking can help you assess the worth of your investment and gauge the degree of competition. Follow the recommended iconnect for more info including cyber security website, cybersec consulting, information security information, technology and cyber security, network security software, network security tools, cybersecurity consultancy, information security and, cybersecurity and ai, cyber security risks and more.